Security information for safe digital utilization delivered by Canon MJ Cyber Security Information Bureau ESET Points of security measures that should be reviewed according to changes in work style
IT environment changed by Korona-ka
Interest in cyber security is increasing year by year. The increasing trend is clear when the number of words including "cyber" used in the minutes of the Diet since 2000 is illustrated (Fig. 1). The summit (Group of Eight) was held in Okinawa in July 2000, when the word "cyber" was used for the first time in the history of the summit. It was in 2013 that the number of such appearances surged. Cyber security was mentioned in the national security strategy and attracted attention not only from the technical aspect but also from the security aspect. After that, the Japanese security industry progressed against the backdrop of the case where the Japan Pension Service was hit by a cyber attack in 2015.
Figure 1: Cyber security trends
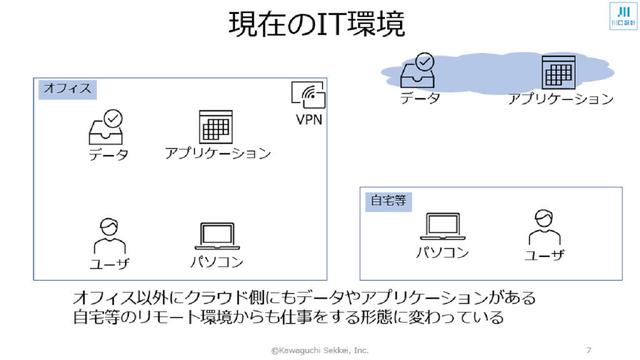
With the spread of the new coronavirus infection, remote work has been recommended, and many companies are now taking it for granted that online conferencing using a web conferencing system is being held. Under these circumstances, the IT environment and security situation of companies were greatly affected. In the conventional IT environment, in principle, all resources such as personal computers and data are in the office, and it was assumed that they would go to work and use them. On the other hand, nowadays, in order to deal with the Korona-ka, an environment where work can be done remotely, such as at home, has been established. Some IT assets remain in the office, but data and applications are being migrated to the cloud.
Figure 2: Current IT environment
The IT environment has changed drastically in just one year due to the Korona-ka, and the current situation is that internal rules and security mechanisms are not able to respond to such situations. Here, we will focus on the three points of "incidents of remote connection terminals", "incidents of cloud environment", and "appliance connected to the Internet", and explain the points to be reviewed.
Incident of remote connection terminal
First, I would like to discuss the problems of remote connection terminals, taking as an example the incident that occurred when the operation consignment company was managing the business system of the user company (Fig. 3). Until now, when performing maintenance work, the person in charge of the operation consignment company was connected to the corporate network to carry out the work. It is a flow to go to the site with a maintenance terminal, install an update file, and update the system.
Here, a problem occurred in supporting remote work by Korona-ka. To protect its employees, the outsourced operator wanted to connect remotely to a maintenance terminal so that they could work without having to go to work. As a result, we assigned a global IP address so that it could be accessed from the outside, and set a weak password. After that, the administrator password was broken, leading to information leakage due to unauthorized access.
Figure 3: Incident due to work mistakes of an operation consignment company
From the client's point of view, they may be dissatisfied with the outsourced operator who has neglected basic security measures. No matter how much the security of the business system is improved, it is meaningless unless the person in charge of the operation consignment company is sufficiently educated. However, there is a different perspective from the perspective of the operation consignment company. Despite the fact that the operation work content has not changed, it is difficult to always assign experienced engineers in the current situation where the operation consignment cost is reduced every year. In addition, even if you want to promote remote work to protect employees, the user company may be particular about local work and request various documents.
As an outsourcer, you wouldn't want to continue a contract where it's difficult to secure profits. At that time, it will be the orderer's side that is in trouble. In order for user companies to protect their systems and have outsourced operations take basic security measures, it is necessary to reconsider realistic business procedures and contract details.
In addition, the following security incidents related to remote connection terminals have occurred.
1) Open port of personal firewall (FW) configured for internal use
When using a terminal used in the company at home for remote work, there are cases where the firewall settings are left as they are. There is a security risk because the ports that should be closed when connecting to the Internet are open.
2) Vulnerable settings of the personal computer distributed by the system department
Since it was supposed to be used in-house, it has insufficient security settings and is vulnerable.
3) Out-of-maintenance terminal that was replaced in a hurry due to a hardware failure
There is a case where an old terminal that has been depreciated is distributed because the terminal used by the employee has a malfunction. Terminals that are out of maintenance are not properly maintained, increasing the risk of security accidents.
4) The communication environment is vulnerable and the update has not been applied.
Communication status is not sufficient in the remote work environment, and Windows updates and other application updates have not been applied. Alternatively, it has been put off and is in a vulnerable state.
Companies that promote remote work should check the firewall settings, etc., in addition to the terminal update status and remote connection settings.
Cloud environment incident
Many companies have started to use cloud services and SaaS (Software as a Service), as represented by Web conferencing systems, but there are cases that have led to security incidents. It is a cloud service or task management system used for information sharing, and access control settings are not appropriate, and information is unintentionally disclosed. People who have started using cloud services that can be used for free in business may have a certain understanding of those security risks, but as they expand their use within the company, they will have sufficient knowledge and awareness of security. It is often the case that confidential information is disclosed by someone who is not.
Some may think that such incidents should be seen and heard and the use of the cloud should be banned. However, we must consider whether we can meet business requirements without using the cloud. Employees used cloud services because of the advantages that existing in-house systems could not provide and the speedy introduction. Even if cloud services are banned unnecessarily, business will become inefficient, and there is a risk that overtime hours will increase and shadow IT that hides and uses cloud services will be rampant. It is desirable to consider and promote a method that can be used safely in-house, rather than prohibiting cloud services uniformly.
Here, I would like to introduce a case where personal information was stolen from a cloud environment (Fig. 4). One company had a general configuration of running a web server on the cloud and storing personal information in a database. The attacker first stole the API key required to operate the cloud environment and launched a virtual machine into the cloud environment. Since the database can also be accessed from virtual machines on the same network, the stored personal information has been stolen. And since the virtual machine was deleted after transferring the personal information, no trace was left.
Figure 4: Hand-Off Stolen Information
The key to this incident is where the API key to access the cloud environment was leaked. In reality, the cause was that the directory on the Web server was accessible from the Internet (Fig. 5). Many companies use Git as their source code management system, but sometimes they include API keys and database connection information in their source code. In this incident, the API key was stolen from a public Git directory.
Figure 5: .git directory browseable
The person in charge of the Web server may have decided that the risk is not high, even though he knew that the directory was open to the public. However, there are many incidents in which information that should not be disclosed, such as API keys, is leaked and misused, so it is necessary to take measures. For example, on a server or personal terminal, the password may be described in a text file. It is possible that the authentication information remains in the script for system management or the configuration file delivered by the vendor. From the attacker's point of view, it means that passwords can be easily obtained and conditions are in place to launch attacks on multiple systems.
Assuming that the use of cloud services will continue to increase, it is necessary to consider shadow IT management and authentication procedures. Multi-factor authentication (MFA) should, of course, be introduced, but it's arguable whether to force the introduction of authentication apps when using personally owned mobile devices. .. Also, considering the current situation that many people reuse the same password for multiple cloud services, we would like to consider introducing single sign-on and ID linkage.
In addition, user education on cloud services is indispensable. At the very least, I would like all employees to be informed and thoroughly ensure that internal information is not shared at URLs that can be freely accessed by people outside the company. For more complex settings, I would like to consult with a system department or security expert.
Appliance to connect to the internet
In recent years, security incidents targeting appliance products that connect to the Internet, especially VPNs (Virtual Private Networks), have become conspicuous. With the spread of remote work, the number of employees connecting from home to the company network via VPN has increased, so it is difficult to set the service downtime for VPN products. In other words, it is conceivable that the operation to update the VPN has not been defined and the update has not been completed.
If it is intruded from an appliance that connects to the Internet, malware etc. are likely to be spread inside, so there is a risk that the damage will spread. Even if the appliance is updated after it has already invaded the inside, the attacker cannot prevent the attack because it has a mechanism to invade again. You should also verify that your account hasn't been created incorrectly and that you need to restart your appliance.
A security expert lists products that ransomware attackers can easily target. Major products such as Microsoft are mentioned, probably because they are targeting organizations where attackers can demand large ransoms. Other companies, such as Capcom, have announced the damage caused by ransomware.
Figure 6: Vulnerabilities targeted by ransomware attackers
Allowing unauthorized access via VPN often damages important IT assets such as ID management servers. Active Directory updates have not been applied, internal communications have not been monitored, and there are not enough protection and detection measures in place. Even if you are prepared for an external attack such as "Do not open suspicious emails", if you are not prepared enough for an attack that has already invaded the inside, the company will suffer a great deal of damage.
In some cases, appliances connected to the Internet are attacked before vulnerability information is announced or patches are applied. Therefore, it will be necessary to take an approach that not only prevents attacks but also detects attacks promptly. The security features of the appliance have to rely on vendor-provided features, and while it is not easy for users to change log settings, it is up to the user to analyze the logs to detect suspicious activity. I want to consider it. Also, depending on the budget, there are ways to introduce IPS (Intrusion Prevention System) and WAF (Web Application Firewall).
Companies that use appliances that connect to the Internet want to take measures from the perspectives of "defense," "detection," and "response" (Fig. 7). First, from the perspective of "defense," it is recommended to consider whether it is possible to limit the IP addresses and users that connect to the VPN. It may be difficult to limit IP addresses to support remote work, but it is possible to review it by limiting users who are not normally using it. In addition, the system department needs to put in place a system to monitor VPN update information. You may not notice the update information until the damage spreads, such as if you are not in a contract with an outsourcer.
Figure 7: Points to review
Next, from the viewpoint of "detection", we would like to establish log output settings and monitoring system. For example, if the VPN log is sent and saved on another server, even if the system is compromised, it is not easy to delete the log on the other server, so the log can be verified. In some cases, you may be able to detect a VPN product problem when you stop sending logs. If you have people to monitor your logs or a company that doesn't have the budget to outsource, consider whether you can automate log analysis.
Finally, from the perspective of "response," I would like to confirm that there are procedures in place to stop the VPN server in the event of a cyber attack.
How to protect uncareed areas
In the security industry, there are many concepts and excellent technologies that attract attention like Zero Trust, but the reality is that there is no solution that can solve everything with one measure. Problems are caused by the elements that make up the system that have not been adequately addressed. Even if security products are installed, for example, if an OS that is out of support or a terminal that has not been updated is left unattended, it often leads to a security incident.
Figure 8: The reality surrounding the system
In corporate systems, security risks are scattered in so-called "non-profitable services". In the "profitable service", measures are taken by aggressive security investment, and in the "deficit service", the system will be stopped because it will be withdrawn early. However, security tends to be postponed for services that are slightly profitable but are not expected to grow significantly in the future. As long as it contributes to the company's profits, it is very difficult for IT and user departments to make the decision to change the system. And while security measures are delayed, they can be attacked and have a tremendous negative impact on company-wide systems and services. I would like the management who has a bird's-eye view of the entire company to verify that the security measures are sufficiently implemented for a system that is operating stably, although the profit is not high.
There are many cases of cyber attacks starting from overseas systems and unmanaged devices. Even if the application you use is protected by the latest security equipment, it does not make sense if it is compromised by another system. Although it is possible to protect the new business environment according to the idea of Zero Trust, it is difficult to extend the scope to existing systems. For "non-profitable services," consider an approach that introduces only a detection mechanism that monitors logs, even if the defense mechanism cannot be strengthened.
in conclusion
In many companies, the process of careful planning, approval, and countermeasures will be common. Due to the Korona-ka, changes in the IT environment and external environment are accelerating, and the requirements and business structure required for business have also changed significantly. Therefore, it is important to leave room for flexibility in responding to changes while proceeding with the planned plans.
In addition, since cyber security measures cannot be implemented by the system department alone, cooperation and collaboration between departments is indispensable. Of course, it is not the purpose of dividing roles by department, but it is important to be conscious of protecting the services and systems provided by the company while improving the efficiency of operations. Under the leadership of the management, I would like the system department to play a central role in promoting security measures that suit the future.
Seminar video is now available!