Conversation: Hitachi studio x Ctrix dangerous, problematic, much-needed telecommuting IT department and employees can feel at ease in the environment manufacturing method-Nikkei Cross Tec Special
-the impact of the new corona, telecommuting / telecommuting suddenly became popular, however, in the emergency system of enterprises, a variety of "flaws" began to emerge. Specifically, what exactly happened?
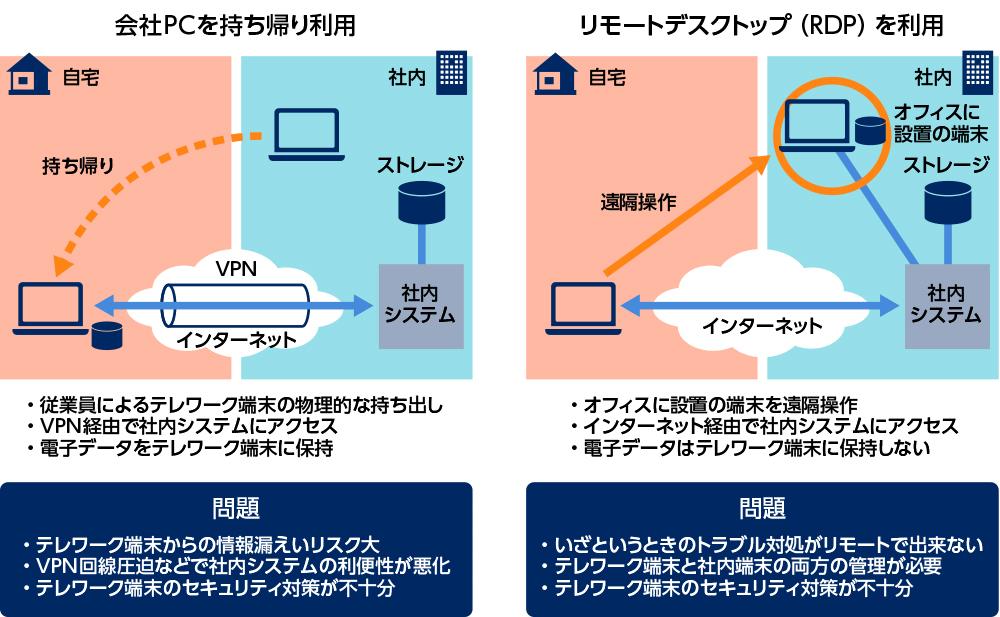
株式会社 日立製作所ITプロダクツ統括本部プロダクツサービス&ソリューション本部エマージングビジネス推進部主任技師幕田 好久氏Mr. Mutian is eager to transfer to companies that work from home, and many companies choose to take the company's PC directly home and access the company's internal systems through VPN. However, if there is a sharp increase in access to VPN lines and it is difficult to connect with the company's internal systems, the behavior of downloading and saving internal and customer information within the PC will increase, which leads to the risk of information leakage from the terminal.
Sometimes they will avoid the VPN that is difficult to connect and send e-mails to customers from their own Wi-Fi and so on. If there is malware lurking in the PC, the customer enterprise may also expand the infection. The cost of enhancing VPN lines is unexpected, and even with security patches on the device, there will be a lot of situations that can't be completely done, because users have to deal with them themselves.
There are also many enterprises that import the remote Desktop (Remote Desktop Protocol:RDP) environment from their own PC to the company's PC for remote operation. RDP is a relatively inexpensive and easy-to-deploy solution, but it cannot handle failures remotely in an emergency.
In the case of an operating system crash, the administrator can only go to the company to restart PC, so it is very troublesome. In addition, in fact, if you work from home in RDP, there is a lot of traffic, and you can't work as you want on your own network line. You have to prepare two terminals for your company and your own home, which will also lead to the increase of management burden.
Figure 1 Common ways and problems of working remotely
In the emergency remote operation of bringing the company's PC home, the VPN line was tight and the convenience of the company's system deteriorated. RDP is the structure of remote operation office PC, but it can not handle faults remotely, so the application and management of the terminal has a heavy burden. In either case, the security countermeasures of the terminal are easy to become inadequate.
[click on the picture to enlarge]
-because both of them are methods of using physical terminals, it is a big task to deal with, run and manage and ensure security in the event of terminal problems. Taking the coronal disaster as an opportunity, the reform of working methods is expected to make more and more progress in the future, but as the basis of its IT, VDI (Virtual Desktop) is now attracting a lot of attention. What is the reason for that?
Mr. Mutian's untroubled advantages such as security and terminal management are evaluated. VDI is a mechanism that provides a virtual desktop environment on the server and transmits the screen to your client device over the Internet. Because the equipment does not have data, it has an advantage in protecting important information assets.
Operating system updates and security patches can also be carried out centrally on the administrator side, even if the administrator works at home. Users can always use a unified and up-to-date environment when the terminal starts, extricate themselves from the tedious maintenance work of PC and focus on the business they are supposed to do. When adding devices as the number of users increases, VDI is based on virtual machines, so it does not increase the burden on managers.
Machang's VDI has the characteristic of low network load. Between the terminal side and the VDI infrastructure, only encrypted and compressed desktop picture differential information and control data are exchanged, and the traffic is less.
It seldom oppresses bandwidth in general business. VDI originally has good security, but there is also a solution with digital watermarking function, which can leak information by shooting the device screen.
This displays the user name, terminal IP address, connection time, etc., in the screen image of each desktop. If the image is leaked, you will immediately find out who is the source of the information. It has a great effect on improving users' security awareness and restraining prohibited behavior.