ASCII.jp What is the business PC protection product "PC MATIC PRO" for "More 1900 days or more Malware infection"?
Cyber attacks aimed at companies frequently occur, and the attack method is becoming more sophisticated and sophisticated.In such a difficult situation, there are PC security products that have achieved zero infections of malware and ransomware for more than 1900 days."PC Matic Pro" is a US -made integrated endpoint security suite.
The PC Matic Pro has implemented a strong security of the "White Listy method" that does not launch any application that has been confirmed in advance, in a practical form that does not take much effort to the administrator, and has attracted attention.There is.It has already been introduced by US government agencies, general companies, and major domestic companies, protecting more than 100,000 corporate endpoints.
In addition to endpoint protection functions, the functions of EDR (endpoint threat detection & support) and RMM (remote terminal operation management) are all -in -one, so it is highly cost -effective and easy to manage management.It is also characteristic.In this article, let's look at the technical features of PC Matic Pro and the benefits of corporate endpoint protection.
"PC Matic Pro" is a US -made integrated endpoint security suite
Advantages and issues of the "White List method" that realizes reliable protection
PC Matic Pro is a corporate integrated endpoint security suite for Windows, MacOS, and Chromebook.The first feature is the adoption of whitelist security.
Common security products, including “next -generation anti -virus products”, adopt a “blacklist system” that is the opposite of whitelist method.Malware, ransomware, and other unauthorized programs are registered on a blacklist (so -called "signecha"), and based on that, detection, block, and deleted.However, now that new species / subspecies of malware and ransomware are produced in large quantities every day, registration on the blacklist has always turned backwards and has not been completely prevented.
On the other hand, the White List Security "refuses" the start of all applications / programs by default, and exceptionally only "permits" the starting in the white list in advance.If you register in advance and register only applications that have been confirmed safety on a whitelist, malware, ransomware, and other fraudulent programs will not be able to start even if the user will start up, and the attack fails.do.As a result, a very strong PC security can be realized.
For example, the US Ministry of Defense (DOD) formulated as a requirement for procurement for defense industries (CMMC) 1.In "0, it is required to implement a" white list application execution restriction "as the highest level (level 5) authentication requirements.In the national defense world, which is targeted for advanced targeted attacks, high -strength security, such as a whitelist method, is needed.
Difference between white list method and blacklist method
However, there are also issues in the White List method.That is, "it takes time to manage the list."
As mentioned above, if the application is restricted to start the application with a whitelist system, it will not be able to execute anything other than the listed application.However, ordinary companies use dozens to hundreds of applications, and it is a lot of effort that administrators know it and register a list by hand.Furthermore, the hash value changes depending on the update even in a legitimate application, so the white list must be updated each time the update is updated.
No matter how strong the security is, it takes a lot of time to operate, and if the end users in the company say that the app cannot be launched, it will not be a practical solution.
Eliminate issues with "application white list" analyzed by malware analysts
The PC Matic Pro has resolved these white -list issues with a new method called "Application White List", significantly reducing the burden on administrators.
What is an application white list?PC Matic series products have already been introduced to more than 3 million PCs for corporations / individuals.Collect more than 100 million application information used in these PCs, and, based on AI scoring, the malware analyst finalizes safety on hand and add it to this application white list.And this list is shared (distributed) to all users.
In other words, the generally used applications are already registered on the white list through this mechanism, and it is not necessary for the IT administrator of each company to register individually.It is a mechanism that creates a list of safe applications with a “collective knowledge”.
Collect the latest application information from users, register for all safety, register, and to users
Let's look at more specific movements.On a PC where the PC Matic Pro is installed, refer to the whitelist and blacklist before starting the application to determine the permission / rejection of execution.Applications with confirmed safety are registered in white lists, and the applications that have been confirmed to be identified, and the applications with vulnerabilities have been confirmed in blacklists.As described above, the processing in the PC is only to "determine whether or not to execute it by referring to the list", so the load is small and does not hinder the light operation of the OS or application.
So how do unknown applications that PC Matic Pro yet knows yet?By default, unknown applications are rejected by judging that there is a danger "gray".At the same time, the application is transmitted to the PC Matic cloud, and the malware analyst performs digital forensic on the cloud to verify safety.
This verification work uses AI / machine learning engines, about 30 kinds of security engines, and sandboxes, but eventually security experts can be performed.It takes 5 minutes to 24 hours to judge, but the application that has been confirmed to be secure is additionally registered on the application white list and can be launched.
In addition, in recent cyber attacks, scripts that abuse PowerShell are used as "file lesumaru wear".PC Matic Pro also provides white lists for these scripts.In addition, a white list method is applied to applications, API calls, communication ports, and file extensions that are started via "Microsoft Office", and only those whose safety has been confirmed is executed / permit.There is.
By applying such a strong restriction, PC Matic Pro has realized the "Malware Ranswear infection zero" for several years mentioned at the beginning.
Unknown applications are determined to be "gray", and all of them are rejected.If safety is confirmed by digital forensic on the cloud, it will be added to the white list and can be started.
Suitable for old systems that are light and supported by manufacturing sites and social infrastructure
If you are not registered in the application white list, such as your own application, can be added to the white list by the administrator himself.Also, if the application that is registered in the blacklist must be used due to vulnerability, the administrator switches the operation mode of the PC Matic Pro (relieving the limit).can do.Although the security strength is reduced, the hulistic detection (a theater detection) is applied in this case, and the application that performs suspicious movements is blocked.
As mentioned above, PC Matic Pro is lightly operated and supports Windows 7, which is supported.Therefore, it can be used effectively on PCs that have to continue using old OSs in the manufacturing factories and social infrastructure sites.In recent years, more advanced security has been required in these sites, and whitelist PC Matic Pro is a highly suitable security product.
The PC Matic series also has a lineup of "Ransomware Lifeline", which operates as an "additional security layer" if you have to continue using existing endpoint protection products (EPP).In other words, by introducing it in combination with other companies' malware countermeasures, you can add a strong white list method to protect the terminal from ransomware and new species malware damage.If you can't remove existing EPPs on a policy, it's a good idea to first consider the introduction of Ransomware Lifeline.
EPP + EDR + RMM all -in -one, cloud management is also a major feature
Another feature of PC Matic Pro is that not only the EPP (endpoint protection) described above, but also EDR and RMM functions are provided all -in -one.At the same price as other companies' next -generation anti -virus products, all functions required for internal terminal management are standard equipment, and cost performance is high.
In EDR, the process on the terminal and the detailed operation logs on the script are recorded / accumulated in the cloud, so if you are damaged by cyber attacks or ransomware, you can quickly investigate the cause and grasp the damage expansion.。There is also a function to acquire a list of processes operating on all terminals in the company, and forcibly prohibit the use of applications for rules.
In addition to such a post -response, it also has a function to prevent damage from potential threats.For example, a security hole driver or an automatic update function of major applications.You will be released from the need to call on tools such as "Adobe Acrobat Reader" and "Filezilla" into the company.
EDR (endpoint threat detection & support) function screen.Process operation logs can be referenced to details such as arguments.It is also possible to launch unauthorized applications from the process list of the entire organization.
RMM provides endpoint asset management functions.It is possible to remote information such as detailed hardware information, installed application information, CPU load status, and memory / storage usage.Administrators can also receive alerts on the lack of resources and security of each terminal.As a unique function, comparing the operating status data of the PC with user PCs around the world, the "world rank", which indicates how much the "comfort" of this PC is, can be displayed.It will help you find a terminal with poor productivity.
In addition, for example, by linking with Active Directory, it is possible to install PC Matic Pro at once, or execute PC operation optimization processing from remotely.Administrators' support for problematic terminals can also be flexible using remote desktop / remote command prompts and file transfer / deletion functions.
RMM (Remote terminal operation management) function screen.Display a list of introduction apps, drivers, and operation processes
Administrators can operate from remotely to forced installation, update, command execution, and file transmission and reception.
In addition, these abundant functions are organized in cloud -type management consoles, which is a great advantage.If there is a console for each product, the management work tends to be wasted, but PC Matic Pro is convenient because it is all integrated.Utilizing the characteristics of cloud -type management, it is also an advantage that the corona is required to be compatible with zero -trade network, even if users and administrators are working at home remotely, they can monitor and manage them in the same way as they are in the company.。
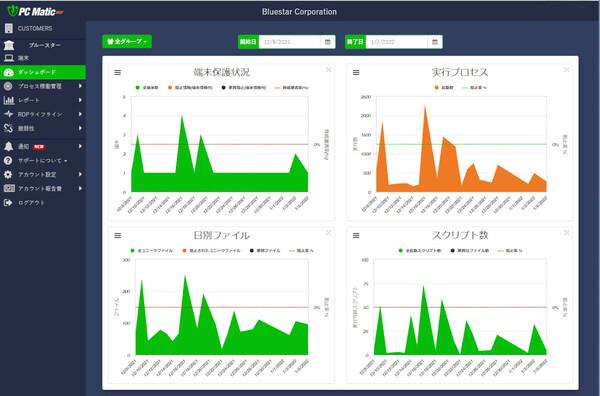
Operating dashboard of PC Matic Pro.Information on EPP + EDR + RMM is summarized, and you can list the terminal protection status and the malicious process / files / scripts that have been prevented.
Supporting customer companies with professional support in Japan, first introducing verification for free
As we have introduced so far, PC Matic Pro is an integrated security suite with very rich functions.However, some IT administrators may be worried that they can use it in -house.For companies with high specialty IT / security personnel, such anxiety will be particularly large.
Therefore, Blue Star, which sells and supports PC Matic Pro, offers a variety of professional services for customer companies.For example, individual analysis of files that the customer obtained (or infected) seemed to be obtained (or infected), monitoring EDR collection logs by experts, early detection / notification of malicious behavior, and supporting local analysis and extermination in the event of an internal infection.We provide paid services.
In addition, the company has a lineup of "PC MATIC MSP", which can provide PC Matic Pro function as a managed security service (MSS).It is said that in Japan, office equipment dealers and managed service providers have introduced this to operate customer PC operation management business.
Blue Star offers a 30 -day free verification program for PC Matic Pro.First of all, apply for verification from PC Matic Pro product site and touch on its ability.
(Provided: Blue Star)