ASCII.jp How to Hack the IoT of Capsule Hotels and Fool Noisy Neighbors
Nowadays, the number of convenient and inexpensive IoT devices is increasing around us, and the number of services using such IoT devices is increasing even in facilities shared by an unspecified number of people such as hotels. However, there are many IoT devices that have been manufactured without fully considering security requirements at the design stage, and there are many cases where the introducing side is operating in a vulnerable state while overlooking security measures.
At the security conference "Black Hat USA 2021" held in August this year, there was a lecture session that introduced an example of such an "IoT problem". In this first part article, I will introduce the contents. In the second part of the article, I would like to report on the results of the author's on-site verification of the content of the lecture and consider this issue.
"Black Hat USA 2021" Casper's lecture title is "Capsule Hotel Hacking-Bedroom Ghost"
Should I stay at a comfortable capsule hotel ...?
Two years ago, going back to now. Casper (handle name), a security consultant for French security company LEXFO, took a long vacation and went on a sightseeing trip to a certain country. His accommodation is a capsule hotel.
The state-of-the-art capsule hotel has been devised so that you can spend comfortably even in a very small room. He liked that it was enough to sleep alone (and it was cheap!), So he decided to stay for several days and enjoy sightseeing from there.
A capsule hotel where Mr. Casper stayed
However, a problem occurs at 2 o'clock in the middle of the night. The phone rang in the capsule next door, and the guest next door started talking loudly. The guest is staying for consecutive nights like Mr. Casper. "Sleep on vacation is a cherished sect," said Casper, who never went to the next room and asked him to mute his voice a bit.
Fortunately, the guest next door agreed with two replies. Mr. Casper who was relieved. However, a few days later, at dawn, the phone rang again, and the neighbor was busy talking in the same loud voice as before. Please forgive me ...
Mr. Casper was really irritated. The "iPod touch" that was given to him at check-in jumped into his eyes. At this capsule hotel, the remote control app installed on the iPod touch can be used to control the lighting inside the capsule, turn the fan on / off, and recline the bed.
At security conferences such as Black Hat, many lectures have been given to point out and report vulnerabilities and bugs in IoT devices such as hotel room iPads and Internet-enabled TVs. Perhaps there is a vulnerability here as well, and it may be possible to mischief neighbors ...
Casper got up in bed and started the investigation.
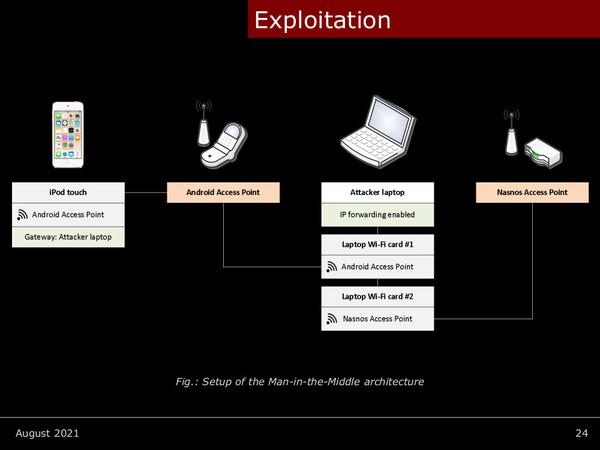
Figure of Mr. Casper who is irritated by his neighbor.It will be such a face, right?
Wi-Fi of IoT controller is vulnerable "WEP" setting
Being able to control the devices inside the capsule with the iPod touch app should mean that you're communicating with the controller via Bluetooth or Wi-Fi. Casper ran a Wi-Fi scan while looking inside the capsule. As a result, it was confirmed that a total of 119 Wi-Fi controllers "CS8700" manufactured by Nasnos operating in access point mode are operating.
The CS8700 is a commercial product that allows you to control multiple devices such as lighting dimmers and electric curtains via Wi-Fi. The number of "119" is the same as the number of capsules in the hotel, so it seems that a controller is installed for each capsule.
A Wi-Fi controller "CS8700" was installed in the capsule. It is an IoT controller that can remotely control lighting dimmers and electric curtains from a smartphone app (images are from the website).
If you find the CS8700 manual by Web search, installation examples of "when there is no existing Wi-Fi network environment" and "when there is" are shown. In this case, since the controller of each capsule has an SSID individually as an access point, it is considered that the former configuration is adopted. In other words, the iPod touch provided for each capsule should have a direct Wi-Fi connection to the controller inside the capsule.
Installation example described in the manual. This time, it seems to be the pattern of (1) connecting directly to the CS8700 from the iPod touch via Wi-Fi (the image is from the website).
Looking for more detailed configuration information, Casper tried to access the features of the iPod touch. However, the iPod touch handed over at the front desk is passcode-locked by the "access guide" function of iOS, and only the remote control application can be started. You can't see the home screen without unlocking it, and you can't launch other apps or see settings. Of course, the hotel doesn't give you a passcode.
However, there was a loophole in the access guide function. When the iPod touch battery is exhausted, the power is turned off, and then the computer is restarted, the access guide starts up with the access guide disabled. In other words, if you run out of battery, you can see the iOS settings. Casper used this technique to bypass the access guide and check the Wi-Fi settings. Then, "Wi-Fi in the hotel" and "Wi-Fi of CS8700" were set.
And there was another important discovery. The encryption method used to connect to the CS8700 controller via Wi-Fi was "WEP". WEP is an old wireless LAN encryption method, and the connection password (WEP key) can only use 5 or 13 alphanumerical characters, so it can be easily analyzed using a tool. Therefore, it is now strongly recommended to use stronger and stronger encryption methods (WPA2, WPA3) instead of WEP.
"With WEP, you can analyze the WEP key by capturing about 80,000 packets of encrypted communication between the access point and the device." With that in mind, Casper created JavaScript to execute a large number of ARP requests on the CS8700, which is an access point, and loaded it into the iPod touch to execute it. After a while, the amount of packets required to decrypt the WEP key accumulated, and soon the decryption was successful. I also confirmed that I could use this WEP key to connect to the CS8700 inside my capsule.
Check the operation commands and setting changes of the device
Next, Casper decided to investigate the traffic flowing between the two, what kind of operation command (command) is sent from the iPod touch dedicated application to the controller.
However, he is traveling and does not have advanced equipment. Here, I created an instant MITM (Man In The Middle) environment by combining my Android smartphone and notebook PC. All traffic flowing between the iPod touch and CS8700 is intercepted by the notebook PC in the middle. If the communication isn't encrypted, you should be able to see the commands sent each time you tap the app's action buttons.
When actually observing the traffic, it was found that the CS8700 accepts operation commands on TCP port 8000, and that authentication at the time of connection and communication encryption are not performed in particular. In other words, if the iPod touch you have can connect to the CS8700 in the next capsule via Wi-Fi, you can operate it as it is. Furthermore, since I could grasp all the operation commands, I could easily write a script to operate automatically.
Configure an instant MITM environment with your device
At the same time, I also got a dedicated app that is open to the public on the Google Play store, scrutinized its features, and tried reverse engineering. There was a new discovery here as well.
This app has a function to register the device to be controlled in CS8700. The setting information is sent from the app to UDP port 988 of CS8700 (Remote Configuration Service port of Simple-WiFi UART), but there was no authentication mechanism here either. In other words, this controller is a mechanism that accepts setting changes from an unspecified number of apps connected to the same network. If you analyze the communication of the setting change in the same way as before, it seems that you can easily rewrite the controlled device linked to the CS8700.