ASCII.JP LTE Communication standard vulnerabilities and captures smartphone lines "ghosts exchanges"
On July 27 at the Security Campaign "BLACK HAT USA 2017" held in the United States on July 27, the unicornTeam of 360 Technology, a China security vendor, attacks vulnerabilities affected by mobile phone communication standards (mobile communication standards).The method "Ghost Telephonist" was revealed (a ghost telephone exchange if translated into Japanese).
The execution of the attack is limited under specific conditions, but if it is misused, the attacker will take over smartphone departure and arrival and SMS transmission and receiving without being noticed by the target mobile phone user.can.He pointed out that password reset and two -stage authentication using SMS, such as Twitter, Instagram, and Facebook, could break through.
From the “GHOST TELEPHONIST” attack demonstration video (using the CHINA UNICOM network).You can deprive your smartphone voice call and SMS transmission and acceptance without being noticed by the original owner
Pierce the vulnerabilities hidden in LTE's "CS Fallback" and take over the 2G communication line
The liver of the vulnerability published this time is that there is no terminal authentication process in "CS Fallback (CS: CIRCUIT SWITCHED, line exchange)", one of the communication specifications of LTE.
CS Fallback is one of the mechanisms prepared in the process of evolving from 3G to LTE with a mobile communication standard of 2G.LTE, a low -delay data communication network, has appeared, and VoLTE (VOICE OVER LTE), which enables voice calling (VOIP) service on LTE, has also been developed.However, during the transition period until all mobile base stations (= communication areas) support LTE, LTE -compatible terminals must also support the old control method so that voice calls can be made in the old 3G/2G area.I can't afford it.
For that purpose, CS Fallback was prepared.To put it simply, when the LTE terminal is a distributor of a voice call, if the VoLTE cannot be used, switch mode and temporarily "drop (fall back)" by temporarily "drop (fall back)".It is a technology that allows lines to be connected to 3G or 2G base stations.
However, UNICORNTEAM survey revealed that no terminal authentication process was provided in the specifications in the 2G/3G network connection treatment during CS fallback.Therefore, if the attacker's terminal satisfies specific conditions, it may be possible to take over the line connection as another LTE device."I wonder if the authentication process was not implemented to minimize the delay in fallback processing," said Lin Juan of UnicornTeam.
The flow of communication between LTE mobile terminals (UE) / LTE base station (ENB) / MME (UE mobile management device) / BSC (base station control device) / MSC (mobile communication control station) during CS fallback.The point is that the connection processing to the 2G line is executed with "No Authentication" after being separated from the LTE line.
To put it simply ... "The terminal that comes out of the LTE door needs to be connected to 2G (GSM) in a hurry, so it is allowed to enter a 2G door without a badge (authentication)."
So how do you abuse this vulnerability and become another terminal?UNICORNTEAM focused on interacting between the base station and the terminal.Specifically, each base station intercepts communication (PCH: paging channel) in which a specific terminal calls a specific terminal in the communication area, and at that time TMSI (for individual terminals in each base station within the communication area.Extract the ID to be temporarily granted) and IMSI (fixed ID specific to the terminal stored in the SIM).If you give a response to the MSC (Mobile Communication Control Bureau) with these IDs, you should be able to become that terminal.
However, this method is only used for 2G networks and does not work for 3G.The first process (IMSI/TMSI replacement) to check the terminals in the communication area for both 2G and 3G has not been encrypted, and the "IMSI/TMSI catcher" has long existed.The problem is that after the IMSI/TMSI replacement, the location information of which terminal is in which base station area (paging area), etc. and finally establishes a communication path, and in the case of 2G, between the terminal and the base station.The communication is encrypted in A5/0 or A5/1.These encryption methods have already been found that can be easily executed have already been discovered (from that reflection, 3G adopted more powerful encryption technology).
Lin Juan, who is engaged in wireless communication -related research at UnicornTeam
In fact, UNICORNTEAM has succeeded in taking a line connection with the base station by obtaining TMSI and IMSI, a mobile device within the same LTE base station, and continuing to be a terminal and continuing to respond to the MSC.。At this time, the owner of the target device who is receiving a spoofing attack does not notice that the attacker has been sent (in principle).
"Ghost Telephonist" attack flow.Just intercept the paging channel to extract TMSI/IMSI and continue throwing paging spons on MSC
"Ghost Telephonist" flow of communication during attacks.The attacker's terminal (UE-F) continues to respond and is hijacking communication from the middle.
The target mobile device will continue to communicate LTE, so you do not notice that the attacker is taking over 2G communication.
In addition, it was explained that using the spoofing line to the attacker's own mobile phone can get the target terminal phone number.In this case, the attacker does not bother to intercept the PCH, and can artificially cause CS fallback by simply making voice calls on the target terminal.
By combining the vulnerability of CS fallback and the attack method, you can receive and transmit voice calls to another person's terminal.
This attack is invalid when the target terminal TMSI is updated on the base station.However, according to UNICORNTEAM's Yuway Zen, some telecommunications operators would keep the TMSi as it was if the terminal did not move (unless the connected base station) was left.
In addition, if the "Location Area Update", which returns the connection line from 2G to LTE if the response to the MSC fails in the function on the terminal side, is executed, the connection that the attacker robbed will expire."For this, you can send a jamming signal, block the connection, and regain the connection again in combination with the CS fallback, but if you do it frequently, you may be aware of the owner of the mobile device," said Zen.In addition, the execution conditions for this function vary for each mobile terminal (installed chipset), and some terminals that are easy to succeed in attack and do not.
Yuway Zen of UNICORNTEAM
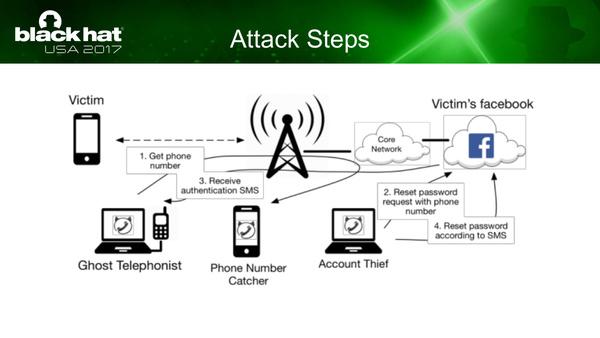
Facebook or Twitter accounts may be deprived of SMS takeover.
In order for the attacks described so far to succeed, the first 2G network (an environment where the A5/0, A5/1 encrypted method is used for easy decoding) is operated as a CS fallback destination.It is a condition.In that regard, 2G services have already ended in Japan, and there is no CS fallback to 2G, so there is no need to worry about linear connection.However, many areas, including the United States, are still providing 2G services overseas.If you go to such an area on a trip or business trip, you may be attacked.It is virtually impossible to prevent.
In addition, for various web services and applications (Twitter, Instagram, Facebook, etc.) that use SMS as a means of password reset and two -factor authentication authentication, the contents of the SMS are stolen through hijacked lines and the account.There is a possibility that you will be deprived.At this time, there is no measure that individuals can do.
It can be applied to web services such as Facebook by collecting SMS and resetting a password.
UNICORNTEAM has already reported this in March this year to the vulnerability reporting window of GSMA, an industry group of mobile telecommunications carriers, and is being responded.
"I hope that the telecommunications carrier implements the authentication process in the CS fallback, and hurry up the spread and response of VOLTE (unnecessary CS fallback). Web services / app operators are mobile terminals (SMS.)